I do a lot of penetration testing for our clients at TechGuard, and each engagement is different and challenging in its own way. The environments change, the maturity of the security programs vary and the goals of the engagement change based on the wishes of the client. One thing I can rely on however are the classics. Those exploits that just seem to work and have been around for quite a while. I’d like to take this blog as an opportunity to discuss one of those such exploits in hopes that our readers will take some action in their own environments to prevent guys like me (as well as those hoodie-wearing bad hacker types) from getting unauthorized access to your network. Now stay with me here because this gets a bit technical, but I’ll try to make it as understandable as possible for the non-technical folks in our readership.
Link Local Multicast Name Resolution (LLMNR) and NetBIOS Name Server (NBT-NS) are two services that are built-in to Windows computers. The purpose LLMNR and NBT-NS serve is to resolve hostnames when the Domain Name System (DNS) fails. Those were a lot of acronyms so let me break this down.
When your computer wants to access another computer on the network, it needs to have its IP Address (kind of like a mailing address for a house). However, it may only know the hostname of the computer it wants to access (kind of like saying Zach’s House). In order to know how to send data to that remote computer it needs to ask for the IP Address by using the hostname (like asking: What’s the mailing address of Zach’s House?). So, who does the computer ask? Why the DNS server of course. The DNS server’s job is to maintain a table mapping hostnames to their respective IP addresses and it will happily answer your computer’s request for a particular hostname’s IP Address… most of the time.
Unfortunately, sometimes DNS resolution fails. It could be that the DNS service had too many requests and couldn’t answer them all in time or maybe there was an issue on the network, or maybe the record of that IP address is missing. The end result is your computer didn’t get the answer to its question. So, what does it do next? Your computer asks its neighbors. LLMNR and NBT-NS are protocols that allow your computer to send out a broadcast message to all the other computers on its corner of the network asking for the IP address of a resource. If a neighboring Windows computer hears the question and knows the answer it will respond and say, “Here you go this is the IP address you were looking for”. Sounds like a great idea, right? Well… what if the computer that is responding to your broadcast isn’t one of your friendly neighbors at all?
Enter Responder.py (https://github.com/SpiderLabs/Responder). Responder is a script that runs on an attacker’s machine and listens for those LLMNR and NBT-NS broadcast requests and happily responds to them. The problem is it that when your computer asks for the IP address of that file server Responder says, “Sure I know the IP address it’s me!” Responder then provides the IP Address of the attacker’s machine to your computer instead of the IP Address of actual file server. Your computer, which doesn’t know any better, then attempts to connect to the imposter file server and passes along a hash of your credentials (sort of like a shortened and encrypted version of your username and password) for authentication. The attacker then captures those hashed credentials and then feeds them into a password cracking server or since a lot of services accept a hash of the users credentials for authentication you could just use the “pass the hash” technique and login without all that password cracking hassle. This is good for pen testers and bad guys, bad for those enterprise defenders out there trying to secure the network.
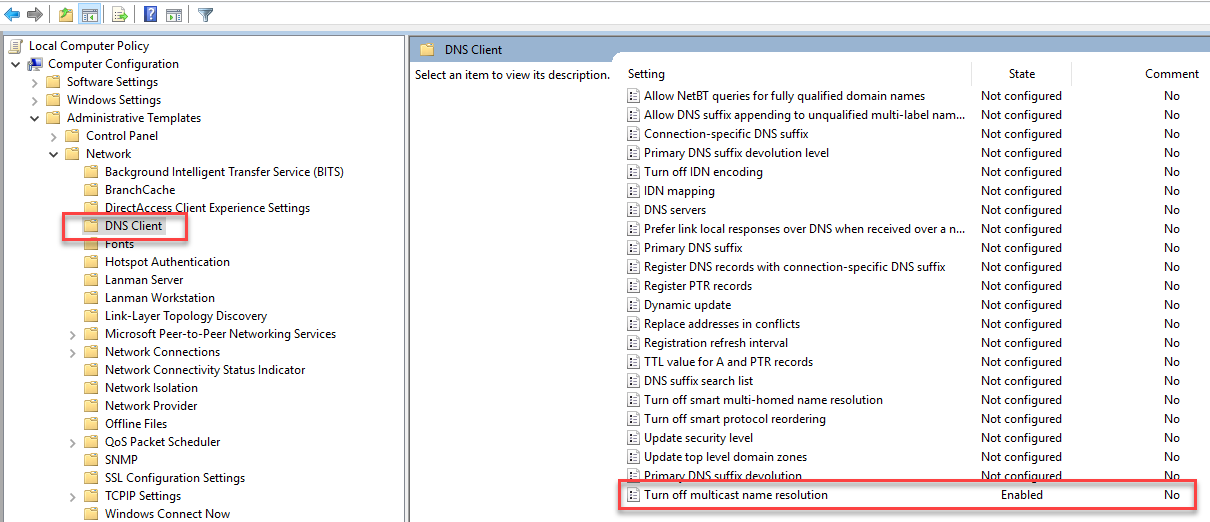
So, what can you do to prevent this from happening? Disable LLMNR and NBT-NS. They really aren’t necessary in modern environments and add additional risk. You should, however, ALWAYS test configuration changes in your network before pushing them out enterprise-wide. It’s a simple task to disable LLMNR via group policy under Network->DNS Client-> Turn off multicast name resolution: set this to Enabled.
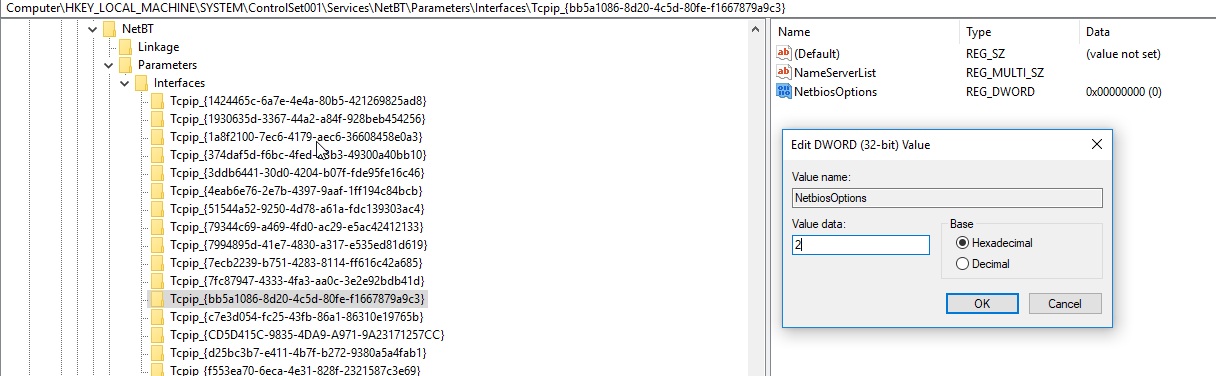
To disable NBT-NS, simply push a registry change to the NetBIOS options for the network card(s) of your machines. Change the value of NetbiosOptions from 0 (default) to 2. This can also be scripted via PowerShell or incorporated into the default image used to create workstations/servers in your environment.
Sometimes simple security hygiene like starting off with a workstation image that is locked down utilizing a security framework such as Center for Internet Security (CIS) Benchmarks can stop an attacker in their tracks.
For information about our penetration test or vulnerability assessment services take a look at our service offerings and contact us today.





