Universal Plug and Play (UPnP) has been a security nightmare since its inception over a decade ago. This technology is generally found in consumer-grade networked devices and allows them to discover other UPnP devices automatically on the network to establish lines of communication as well as broadcast the services that the device may provide to the rest of the network. A very convenient service, UPnP enabled devices can join a network and announce the services it offers without the need for users to configure anything.
Sadly convenience is often at odds with security, and this case is no exception. UPnP enabled routers, for example, if configured to do so (which is the default setting in many routers), will gladly open ports for a newly installed UPnP device on the network if it requests. That again would be very convenient for the non-tech savvy consumer. However, it opens up the network at the behest of devices that are plugged in, whether they are secure and trusted or not. This is certainly not a security best practice and a long way from Zero Trust Security even for a home network, and as we know the importance of securing home networks is becoming greater and greater in a post-COVID-19 world.
In addition to the insecure intended function of the protocol, there have been several unintended security holes in UPnP over the years, some of which have been pretty bad, and now we have a new one... Enter “CallStranger” tracked as CVE-2020-12695, which is a server-side request forgery (SSRF) affecting just about everything that can utilize UPnP (smart devices, routers, IoT, laptops, and more). The vulnerability is in the “SUBSCRIBE” capability of the protocol. Basically, the attacker sends an HTTP request for the “SUBSCRIBE” function, spoofing the requesting IP to that of the intended target. By sending this to a large number of UPnP enabled devices, you can then utilize both the amplification of the request (the response is larger than the request) as well as the distributed nature of the UPnP devices to create a substantial Distributed Denial of Service (DDoS). There is also the risk of scanning internal ports on your network from internet-facing UPnP devices discussed by Daniel Garcia at Defcon 19.
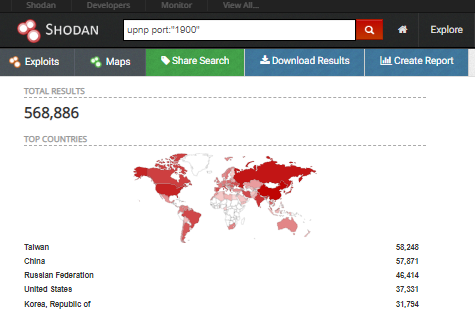
CallStranger was discovered by a Turkish researcher named Yunus Çadırcı. Yunus points out that vulnerable devices must have UPnP enabled and exposed to the internet, which is a saving grace for a lot of devices, but a quick Shodan search reveals over 500,000 devices on the internet that are potentially at risk. Yunus published the technical report as well as the Proof of Concept (PoC) code on Github.
So how do you fix it? My recommendation is to disabled UPnP in your devices and not look back. The challenge about fixing this issue is that UPnP is an open protocol maintained by the Open Connectivity Foundation. They have updated and fixed the protocol specification; however, it is now up to all of the device and software creators to make that updated specification into a reality with patches.
The ugly truth is that this vulnerability will be around for a long time. Since that is the case, I would recommend disabling UPnP and configure your router or firewall to block all unnecessary ports and protocols as well as ensure that UPnP is disabled there so that your internal devices cannot open up holes in your network without your knowledge.





