Do you do work with the Department of Defense (DoD)? If so, are you preparing for the “CMMC?” If not, you might want to head on over here and take a look at the draft cybersecurity document that’s on the cusp of being implemented.
The government began the process of creating the new cybersecurity model in March of this year. This model has attracted a great deal of attention considering every contractor must meet these requirements before they bid on any Department of Defense (DoD) work. In late 2020, every government contract organization will need to be certified in some level of the Cybersecurity Maturity Model Certification (CMMC) in order to bid on Requests for Proposal (RFP’s). This is a big deal because current requirements use the NIST 800-171 standard which has a “self-assessment” option available. Self-assessments are not the greatest judge of compliance when it comes to cybersecurity. In order for companies that work with the DoD to step up their game, the Office of the Under Secretary of Defense for Acquisition and Sustainment is moving to standardize cybersecurity across the supply chain. The new CMMC model will use a certification process that will be implemented by trained third party attesters. This approach will add consistency and oversight to a largely “personally accountable” compliance model. Below are some of the more important dates to know about.
CMMC Timeline of Implementation (upcoming dates)
• CMMC ver. 0.6 – Nov. 2019
• CMMC ver. 0.7 – Dec. 2019
• CMMC ver. 1.0 – Feb. 2020
• Training of 3rd party assessment organizations for CMMC – Jan. to June 2020
• CMMC to start appearing in RFIs – June 2020
• CMMC to start appearing in RFPs – Sep. 2020
How will the CMMC work?
What we currently know about the draft certification guidelines, is that
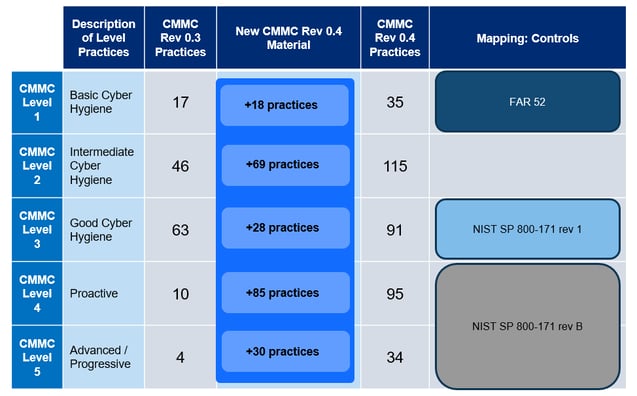
there are multiple levels of compliance based on the maturity of the company. Each of these levels has a specific number of practices and processes in the 18 domains covered in the CMMC model. Each practice will need to be adhered to in order to gain that certification level. A number of these controls map directly to the current cybersecurity standard being used under NIST 800-171. Also, each of these controls will use a “go / no go decision.” This means that there will be no partial credit when considering if the control is implemented or not. A general understanding of each practice level can be found below.
Level 1 – “Basic Cyber Hygiene”
35 CMMC Rev 0.4 Practices – These are items are basic controls like implementing account lockouts for users on workstations. Collection requirements for audit logs & ad hoc physical access control processes are also considered.
Level 2 – Intermediate Cyber Hygiene”
115 CMMC Rev 0.4 Practices – These items consist of slightly more advanced controls like separation of duties for user accounts, automated software inventory tools and systems and data recovery processes.
Level 3 – “Good Cyber Hygiene”
91 CMMC Rev 0.4 Practices – An example of these controls would be limiting of “privileged” activities from the standard day to day access with respect to user accounts. Using passive asset discovery tools and implementing business continuity plans for redundancy and availability are also part of this set.
Level 4 – “Proactive”
95 CMMC Rev 0.4 Practices –These proactive practices require implementing network segmentation and performing penetration testing at least annually. Organizations would also need to ensure offline backups exist as well as testing their continuity controls.
Written by Grant Codak
Grant has over a decade of IT experience spanning a variety of domains with a focus on defensive security. Grant is currently a Cybersecurity Expert at TechGuard Security where he performs a wide variety of proactive security services, including penetration testing. He also holds the following certifications: CISSP, CEH, Security+, Network+, A+, and Metasploit Pro Certified Specialist. Recent responsibilities include, a Senior Web Security Engineer at a Fortune 50 organization along with a variety of application administration roles in security operations. His past project work includes, web tool development as well as firewall and web proxy migrations. Currently at TechGuard Security, Grant conducts audit control assessments, penetration tests, vulnerability assessments and social engineering exercises. Grant ties his knowledge together with his deep understanding of network operations and security architecture to deliver approachable report analysis to clients. Grant is also a nature enthusiast and enjoys mountain biking, hiking and kayaking.





