A remote code Execution has been detected in the wild, known as the Log4j Vulnerability. This vulnerability allows an attacker to have the potential to carry out remote code execution on Java-based apps using Log4j or webservers with Apache Log4j.
If executed correctly, the attacker would have the same level permissions as the Log4j library. Log4j has scored a perfect CVSS score of 10 out of 10, with remediation recommended immediately.
To help identify if you are vulnerable, first look if systems are running Apache service versions 2.0-2.14.1. If identified follow the below steps. Also see Apache Log4j Vulnerability Guidance.
- Upgrade to Log4j 2.16.0 to remediate this vulnerability.
- Add input sanitization to help with any future issues.
- Set the system property to formatmsgnolookups to TRUE
- Set the formatmsgnolookups to TRUE.
- Remove the JNDI lookup class from the classpath if you cannot fully update to 2.16.
Secondly, pay attention to your vendor released updates and apply once available. To help identify software vendors impacted, see CISA Log4j (CVE-2021-44228) Vulnerability Guidance.
This is an ongoing issue that TechGuard will be monitoring. We will update this page and resources as more information comes out. For further details and recommended actions on this issue, see the CISA alert page created for this vulnerability.
*Update 01/10/2022*
Last month’s discovery of the Apache Log4J library has led to additional updates and multiple other vulnerability disclosures as the severities continue into this year, leaving companies struggling to identify affected systems and implement fixes.
Recently, the Federal Trade Commission, whose primary function is to protect American consumers, has made a new statement to companies that's been drawing headlines. The FTC has warned to take legal action against any companies in the US jurisdiction that do not take appropriate actions to remediate the log4j vulnerability.
Not following the widely advertised Apache Log4J remediation guidance further not only puts their customers at risk but also risks organizational compliance in terms of laws such as the FTC Act and potentially GBLA.
There have also been newly reported vulnerabilities affecting the open source Log4J library. The National Vulnerability Database has recently published four additional vulnerabilities affecting other versions of Java.
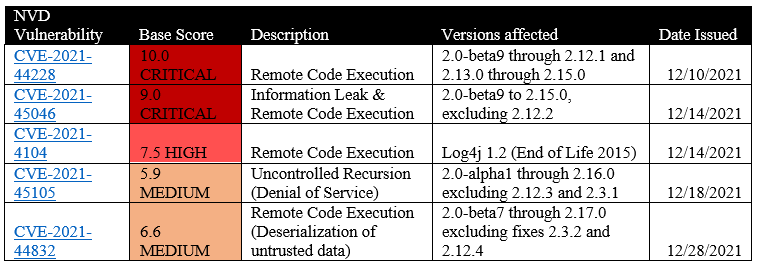
As always with situations like Log4j, please make sure you are paying attention to your vendor updates for any critical patches or remediation that needs to be applied in your environment.
New attack signatures from hackers ranging from script kiddies to the most advanced hacking gangs in the world are being discovered daily. This situation is rapidly developing and is likely to persist far into the new year. If you have any questions concerning Log4j and its potential impact on your organization, please contact us.
Written by Adam Voss

Adam Voss graduated from Maryville University with an emphasis on pen-testing. Currently, he works at TechGuard as a cybersecurity analyst. When he's not working on projects or expanding his knowledge in the field to get his certs, he can be found doing something that involves physical exercise or rooting for the cardinals or blues.




.jpg)
